- Service: Source Code Review
- By: Razz Security IT Services LLP
- Date of Review: October 1–25, 2024
Background:
A client in the education and training sector partnered with Razz Security IT Services LLP to perform a security-oriented source code review for their newly developed ERP web application. The objective was to identify and mitigate potential vulnerabilities before the application was deployed in a production environment.
Review Timeline:
- Start Date: October 1, 2024
- End Date: October 25, 2024
- Duration: 25 days
Review Methodology:
We used a combination of static code analysis and dynamic application testing:
- Static Code Review: Manual inspection of source code for logic flaws, insecure coding patterns, and missing validation.
- Dynamic Code Review: Deployment in a test environment followed by simulated attacks using real-world tools and payloads.
Key Finding: SQL Injection on Login Page
During the review, a critical vulnerability was discovered in the login page. The txtEmail input field was being used directly in SQL queries without any sanitization or use of parameterized statements.
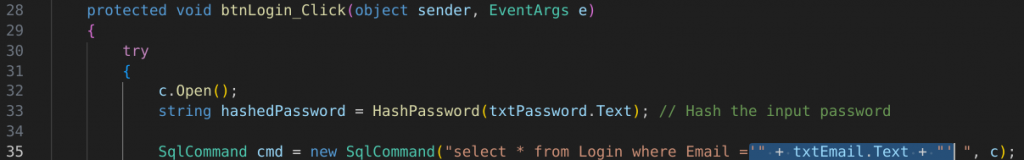
Vulnerability Type: SQL Injection (Critical)
CVSS Score: 10.0 (Critical Severity)
Steps to Reproduce:
SQLMap command used (note that the URL needs to be changed according to the local setup):
sqlmap –random-agent –skip-waf –forms –dbms mssql -u http://172.25.128.1:49978/
Exploit:
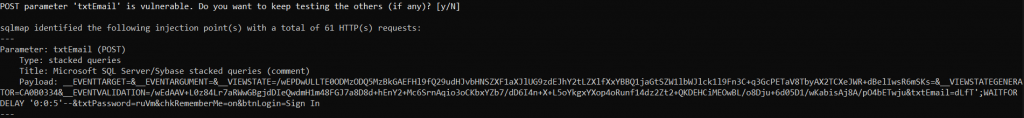
Impact:
If exploited, this SQL Injection vulnerability could allow an attacker to:
- Compromise the underlying server, potentially leading to full system takeover or lateral movement within the organization’s network
- Manipulate database queries, bypassing authentication or altering application behavior
- Extract sensitive data such as user credentials, personal records, and internal business information
- Perform unauthorized actions such as modifying or deleting records
- Gain administrative access to the backend system
Recommended Fix:
We advised the development team to replace raw SQL queries with parameterized queries or utilize secure Object-Relational Mapping (ORM) practices.
// Secure example using parameterized queries
string query = “SELECT * FROM Users WHERE Email = @Email AND Password = @Password”;
SqlCommand cmd = new SqlCommand(query, conn);
cmd.Parameters.AddWithValue(“@Email”, email);
cmd.Parameters.AddWithValue(“@Password”, password);
Result:
The development team implemented the fix promptly. Follow-up testing confirmed that the issue was successfully resolved. This engagement prevented a critical vulnerability from reaching production and strengthened the overall security posture of the application.
Conclusion:
This case study highlights the importance of early-stage source code review in uncovering severe security issues like SQL Injection. Through secure coding practices and proactive testing, organizations can greatly reduce the risk of cyberattacks.
About Razz Security IT Services LLP
We help companies build secure software by offering:
- Static and dynamic source code reviews
- Penetration testing services
- Secure development consulting
- Cybersecurity awareness and training
Need a Security Review?
Ensure your applications are secure before they go live.
Contact us today to schedule a comprehensive source code review or penetration test:
Phone: +91 86187 19868
Email: contact@razzsecurity.com
Website: www.razzsecurity.com

Founder & CEO of Razz Security. Ethical hacking geek, tech innovator, and problem solver. This blog is where I drop insights, research, and hacks to help you stay ahead of digital threats and push the limits of technology.
Leave a Reply